As in my previous post I told you what is the Key-loggers, its types and all other info. Now it is the time to do something practical. Below I listed some Key-loggers, just select one of them download it and install it. Try it fast. As Key-loggers may harm you or you may be the victim of a Key-logger. So protect yourself from being hacked by applying one of the ways given in the keyloggers countermeasures.
 The effectiveness of keyloggers countermeasures varies, because key-loggers use a variety of techniques to capture data and the countermeasure needs to be effective against the particular data capture technique. For example, an on-screen keyboard will be effective against hardware key-loggers, transparency will defeat some screen-loggers - but not all - and an anti-spyware application that can only disable hook-based key-loggers will be ineffective against kernel-based key-loggers. Also, key-logger software authors may be able to update the code to adapt to countermeasures that may have proven to be effective against them.
The effectiveness of keyloggers countermeasures varies, because key-loggers use a variety of techniques to capture data and the countermeasure needs to be effective against the particular data capture technique. For example, an on-screen keyboard will be effective against hardware key-loggers, transparency will defeat some screen-loggers - but not all - and an anti-spyware application that can only disable hook-based key-loggers will be ineffective against kernel-based key-loggers. Also, key-logger software authors may be able to update the code to adapt to countermeasures that may have proven to be effective against them.

An anti key-logger is a piece of software specifically designed to detect key-loggers on a computer, typically comparing all files in the computer against a database of key-loggers looking for similarities which might signal the presence of a hidden key-logger. As anti key-loggers have been designed specifically to detect key-loggers, they have the potential to be more effective than conventional anti virus software; some anti virus software do not consider certain key-loggers a virus, as under some circumstances a key-logger can be considered a legitimate piece of software.
Antispyware Plus Download => Antispyware + serial + crack

Nowadays in market many Anti-spyware, Anti-root kits and Anti-viruses are present which can easily identify the key-logger. After detecting key-logger either they give a pop out to user to uninstall it or they itself disable or remove it. But nowadays key-loggers are coming with a legitimate piece of software, so anti spyware often neglects key-loggers to be virus or spyware.

If you are having Live CD with no malware and viruses, fully secured. Then there is no danger of key-logger. Because the Operating Systems it provides will be fully secured and fully patched, no way of key-logger. So no impact of any key-logger at all.
 You can use smart cards or any other security tokens. Security tokens are used to prove one's identity electronically and grant them access to computer services. it may be a physical device or a software. These are things which improve your security against replay attacks by a attacker through key-logger information. Some security tokens work as a type of hardware-assisted one-time password system, so it is more beneficial to us.
You can use smart cards or any other security tokens. Security tokens are used to prove one's identity electronically and grant them access to computer services. it may be a physical device or a software. These are things which improve your security against replay attacks by a attacker through key-logger information. Some security tokens work as a type of hardware-assisted one-time password system, so it is more beneficial to us.
 In the market you can find the Keystroke Interference software. Some of them are free but some of them are paid. These software just hit random keys at regular intervals or when user actually hits any key manually. So it will confuse key-logger and it will record extra information. Hence it's become hard for hacker to recover the original information.
In the market you can find the Keystroke Interference software. Some of them are free but some of them are paid. These software just hit random keys at regular intervals or when user actually hits any key manually. So it will confuse key-logger and it will record extra information. Hence it's become hard for hacker to recover the original information.

 These are the methods which are non-techie or you can say you have to do it manually.
These are the methods which are non-techie or you can say you have to do it manually.
As you know key-logger records every key. Sometimes what happened is that you by mistake typed the wrong password and in second attempt you typed it right, then this could be identified by hacker and he would filter it out. But typing extra thing or stroking extra keys may help you to counter key-logger.
One of the method is that instead of typing your passwords in the focus or log-in window type them somewhere else like in a notepad and save it. Now where ever you require those passwords just copy and paste from there. By this key-logger won't be able to store anything.
One other method is putting password and user names in wrong order. When ever you required to log-in just type your password in wrong order like first character at last and last character first. By this key-logger will be able to store only un-ordered password. Like you want to type password "secure" then put in this way first type e then use arrow keys to move left to type character r then move left and son on. By this key-logger will store "eruces" which is completely different.
You can use this technique also that put password first then username or put username then somewhere else (notepad) of focus window type random keys then type again password in focus window.
One more technique is that while typing your password just type random keys, thenselect them with mouse cursor and replace by correct character of password. For example your password is "Ansh", then type An after it type random keys "asdf". Now select these "asdf" keys using mouse cursor and type s then h. Now what happens is that you had wrote the correct password but key-logger stores "Anasdfsh", which is wrong password.
This is not effective against advance key-loggers as they also take screen shots and videos, but very useful in basic software key-loggers or hardware key-loggers.
If You are having any query, then mail me or comment here!
If you Like This Post Then Like/Share It!
Keep Enjoying!
Name of Best Key-loggers
Keylogger Countermeasures
 The effectiveness of keyloggers countermeasures varies, because key-loggers use a variety of techniques to capture data and the countermeasure needs to be effective against the particular data capture technique. For example, an on-screen keyboard will be effective against hardware key-loggers, transparency will defeat some screen-loggers - but not all - and an anti-spyware application that can only disable hook-based key-loggers will be ineffective against kernel-based key-loggers. Also, key-logger software authors may be able to update the code to adapt to countermeasures that may have proven to be effective against them.
The effectiveness of keyloggers countermeasures varies, because key-loggers use a variety of techniques to capture data and the countermeasure needs to be effective against the particular data capture technique. For example, an on-screen keyboard will be effective against hardware key-loggers, transparency will defeat some screen-loggers - but not all - and an anti-spyware application that can only disable hook-based key-loggers will be ineffective against kernel-based key-loggers. Also, key-logger software authors may be able to update the code to adapt to countermeasures that may have proven to be effective against them.- Anti Key-logger:

An anti key-logger is a piece of software specifically designed to detect key-loggers on a computer, typically comparing all files in the computer against a database of key-loggers looking for similarities which might signal the presence of a hidden key-logger. As anti key-loggers have been designed specifically to detect key-loggers, they have the potential to be more effective than conventional anti virus software; some anti virus software do not consider certain key-loggers a virus, as under some circumstances a key-logger can be considered a legitimate piece of software.
Antispyware Plus Download => Antispyware + serial + crack
Anti keylogger Download => anti keylogger + serial + crack
The best to way to protect from keylogger is to use quick heal antivirus and spyware doctor antivirus
Quick Heal antivirus Download => Quick heal antivirus + crack + serial key
Spyware doctor antivirus Download => spyware doctor + serial key + crack
- Sandboxie :
- Keyscrambler :
It is the software which encrypts the key as soon as it is pressed. So only key-logger can record is only encrypted keys. Which is of no use until it is de-crypted. But Decryption is not so easy.


- Anti-spyware / Anti-virus programs :

Nowadays in market many Anti-spyware, Anti-root kits and Anti-viruses are present which can easily identify the key-logger. After detecting key-logger either they give a pop out to user to uninstall it or they itself disable or remove it. But nowadays key-loggers are coming with a legitimate piece of software, so anti spyware often neglects key-loggers to be virus or spyware.
No software-based anti-spyware or anti-virus application can be 100% effective against all key-loggers and even against viruses. One more problem is having that these anti-viruses and anti-spywares can't detect hardware key-loggers.
- Live CD/USB :

If you are having Live CD with no malware and viruses, fully secured. Then there is no danger of key-logger. Because the Operating Systems it provides will be fully secured and fully patched, no way of key-logger. So no impact of any key-logger at all.
- Network monitors :
Network Monitors is the software which monitors the network or keep an eye on it. It is also called Reverse firewall. It gives user an alert whenever an application tries to connect the network. With the help of this software user gets a chance to prevent the key-logger from "phoning home" with his or her typed information.


- Automatic form filler programs :
 Automatic filler programs are the software's which detects the form on the screen and fill it automatically. now user does not require a keyboard to fill his personal details and passwords. Hence key-loggers are unable to store anything. These are mainly for web Browsers to fill the long long forms of websites.for web browsers you can add extensions . like one of the best extension is 'Last Pass' it is available for Chrome, Mozilla Firefox and Internet Explorer browsers. It is best for countering key-loggers. It can store the passwords for every website and automatically fills the required information for Log-in and Sign-up.
Automatic filler programs are the software's which detects the form on the screen and fill it automatically. now user does not require a keyboard to fill his personal details and passwords. Hence key-loggers are unable to store anything. These are mainly for web Browsers to fill the long long forms of websites.for web browsers you can add extensions . like one of the best extension is 'Last Pass' it is available for Chrome, Mozilla Firefox and Internet Explorer browsers. It is best for countering key-loggers. It can store the passwords for every website and automatically fills the required information for Log-in and Sign-up.
- One-time passwords :
You can use one time passwords system. In this only one password is to be used once. By this as soon a password is typed and recorded and used by attacker it will show "wrong password". Because user has already used that password. it is safe when you are using public computers. If you are doing any transaction work on public computer I will recommend to do it fast and change the password immediately. Because an attacker having remote control over a computer can simply wait for the victim to enter his/her credentials and soon after he can used his account to do money transfer while their session is active.
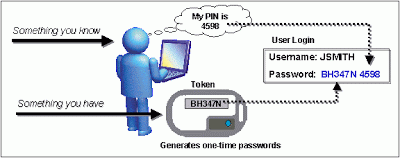

- Security tokens :
 You can use smart cards or any other security tokens. Security tokens are used to prove one's identity electronically and grant them access to computer services. it may be a physical device or a software. These are things which improve your security against replay attacks by a attacker through key-logger information. Some security tokens work as a type of hardware-assisted one-time password system, so it is more beneficial to us.
You can use smart cards or any other security tokens. Security tokens are used to prove one's identity electronically and grant them access to computer services. it may be a physical device or a software. These are things which improve your security against replay attacks by a attacker through key-logger information. Some security tokens work as a type of hardware-assisted one-time password system, so it is more beneficial to us.- On-screen keyboards :
As you know Windows comes with default On-screen keyboards. Windows included On-screen keyboard for the purposes of keyboard failure and security issues. So you should have to take advantage of it. Every time when you have to put password do it by on-screen keyboard. in this what happened is that according to user action respective button is pasted in focused window. For Mac and Linux, the software is available to enable on-screen keyboard. using on-screen keyboard key-logger will not be able to take log any key as you had not typed any keys from hardware keyboard. But this is not helpful for the key-loggers which also took snapshots and videos.
- Keystroke interference software :
 In the market you can find the Keystroke Interference software. Some of them are free but some of them are paid. These software just hit random keys at regular intervals or when user actually hits any key manually. So it will confuse key-logger and it will record extra information. Hence it's become hard for hacker to recover the original information.
In the market you can find the Keystroke Interference software. Some of them are free but some of them are paid. These software just hit random keys at regular intervals or when user actually hits any key manually. So it will confuse key-logger and it will record extra information. Hence it's become hard for hacker to recover the original information.- Speech recognition :
Instead of on-screen keyboards, you can also use speech-to-text conversion software can also be used against key-loggers. Since in this case also no typing hence key-logger will not be able to log anything. The weakest point of using this software is that how the software sends the recognized text to target software after the recognition took place successfully.
- Handwriting recognition and mouse gestures :
Nowadays many tablets and notepads are coming in which which pen or finger movement on their touchscreen understand the text and it is filled in the focus window.
If your computer is not touch screen or not having this feature then you can use mouse gestures softwares, which convert your cursor movement into the desired text. Difference is that here mouse gestures use mouse movement instead of pen in touchscreen.
Or you can use the light Pen or Electronic Pen with help of these pens when you write on monitor screen they understand them and convert to text.
This technique is also having same weakness as speech recognition has.
If your computer is not touch screen or not having this feature then you can use mouse gestures softwares, which convert your cursor movement into the desired text. Difference is that here mouse gestures use mouse movement instead of pen in touchscreen.
Or you can use the light Pen or Electronic Pen with help of these pens when you write on monitor screen they understand them and convert to text.
This technique is also having same weakness as speech recognition has.

- Non-technological methods :
 These are the methods which are non-techie or you can say you have to do it manually.
These are the methods which are non-techie or you can say you have to do it manually.As you know key-logger records every key. Sometimes what happened is that you by mistake typed the wrong password and in second attempt you typed it right, then this could be identified by hacker and he would filter it out. But typing extra thing or stroking extra keys may help you to counter key-logger.
One of the method is that instead of typing your passwords in the focus or log-in window type them somewhere else like in a notepad and save it. Now where ever you require those passwords just copy and paste from there. By this key-logger won't be able to store anything.
One other method is putting password and user names in wrong order. When ever you required to log-in just type your password in wrong order like first character at last and last character first. By this key-logger will be able to store only un-ordered password. Like you want to type password "secure" then put in this way first type e then use arrow keys to move left to type character r then move left and son on. By this key-logger will store "eruces" which is completely different.
You can use this technique also that put password first then username or put username then somewhere else (notepad) of focus window type random keys then type again password in focus window.
One more technique is that while typing your password just type random keys, thenselect them with mouse cursor and replace by correct character of password. For example your password is "Ansh", then type An after it type random keys "asdf". Now select these "asdf" keys using mouse cursor and type s then h. Now what happens is that you had wrote the correct password but key-logger stores "Anasdfsh", which is wrong password.
This is not effective against advance key-loggers as they also take screen shots and videos, but very useful in basic software key-loggers or hardware key-loggers.
If You are having any query, then mail me or comment here!
If you Like This Post Then Like/Share It!
Keep Enjoying!














0 comments: